
Digital Immune System
The Digital Immune System (DIS)
What is a Digital Immune System?
A digital immune system (DIS) is a combination of technologies and practices from software design, development, operations and analytics to decrease business risks. A strong digital immune system makes critical applications and services more resilient so they can recover more quickly from failures caused by bugs, preventing complete shutdown. A digital immune system creates a superior Customer Experience (CX) and User Experience (UX) by being more resilient to failures. A digital immune system is adaptable and keeps evolving continuously, which is similar to a human immune system.
This comprehensive approach to virus protection was developed by IBM to counter the rising threat of internet-based virus attacks. Previously, antivirus software was updated monthly, and this was enough to deal with the threats. Also, initially, the internet played a relatively minor role in the spread of viruses. But, with integrated mail systems and mobile-program systems on the rise, the rate of virus propagation through the internet increased. The Digital Immune System was developed as a response to these internet-based attacks. The objective was to provide a rapid response so that viruses can be neutralized as soon as they are introduced.
When a virus enters a system, the immune system automatically detects it, analyzes it, blocks it, removes it and sends a report to the systems running IBM antivirus software so its further spread can be stopped.
At a biological level, when a virus is neutralized, it loses its ability to create further damage. But, at a computational level, if a system does not evolve in the wake of a threat, it loses its ability to deal with several new threats. So, if a digital system does not adapt to new threats, it quickly becomes absolute and ineffective. Therefore, a complete response comprises detection, prevention, and adaptation.
What Are the Elements of a Digital Immune System?
The preparation for building a digital immune system should begin with a strong vision statement to align the organization. Then, the following practices and technologies should be taken into consideration:
Observability
Building observability into applications provides the information necessary to resolve reliability and resilience issues. Observability of user experience also allows for improvement in UX.
AI-augmented Testing
AI-augmented testing allows companies to make software testing increasingly autonomous. It complements conventional testing by automating the planning, creation, maintenance, and analysis of tests.
Chaos Engineering
Chaos engineering uses experimental testing to find vulnerabilities and weaknesses in complex systems. Teams can use it in pre production environments to safely master the practice and then use it during normal operations.
Auto remediation
Autoremediation is the practice of building context-sensitive monitoring into an application. It automatically monitors and corrects issues after detecting them, returning the system to a normal state without requiring input from staff. It also remediates any failing UX by combining observability with chaos engineering.
Site Reliability Engineering (SRE)
Site Reliability Engineering focuses on improving customer satisfaction by leveraging service-level objectives. It reduces the effort developing teams exert on remediation and tech debt while allowing for better UX.
Software Supply Chain Security
Software Supply Chain Security protects the integrity of internal and external code through the use of strong version-control policies, artifact repositories for trusted content, and management of vendor risk throughout the delivery life cycle. By addressing the risk of software supply chain attacks, software supply chain security improves the visibility, transparency, security, and integrity of proprietary and open-source code in software supply chains.
How Does a DIS Work?
The monitoring program installed on a PC continuously looks for any odd system behavior or suspicious changes to programs or signatures. The monitoring program then forwards a copy of a program it sees as infected to an administrator machine within the organization. The administrative machine, then, encrypts the file and sends it to a central virus analysis machine. The central machine then creates a safe environment within which the infected program can be run for analysis. The virus analysis machine then identifies the virus and develops a code to remove the virus. This code is sent back to the administrative machine. From here, this prescriptive code is sent to the infected PC, as well as to all the other PCs in the organization. Moreover, this code is sent to all the clients as part of regular antivirus updates.
Practical Applications of DIS
The application of DIS is not only limited to detecting viruses. In fact, DIS can be trained to detect any anomaly in a data set in real time. For example, in 2018, Dispatchr Inc. and Hitachi Consulting Corporation, a subsidiary of Hitachi, Ltd., launched the first Digital Immune System designed for electric utilities. This DIS leveraged advanced AI and big data to create a breakthrough in preventing wildfires and power outages caused by extreme weather or equipment failure.
How Croyten Helps With DIS
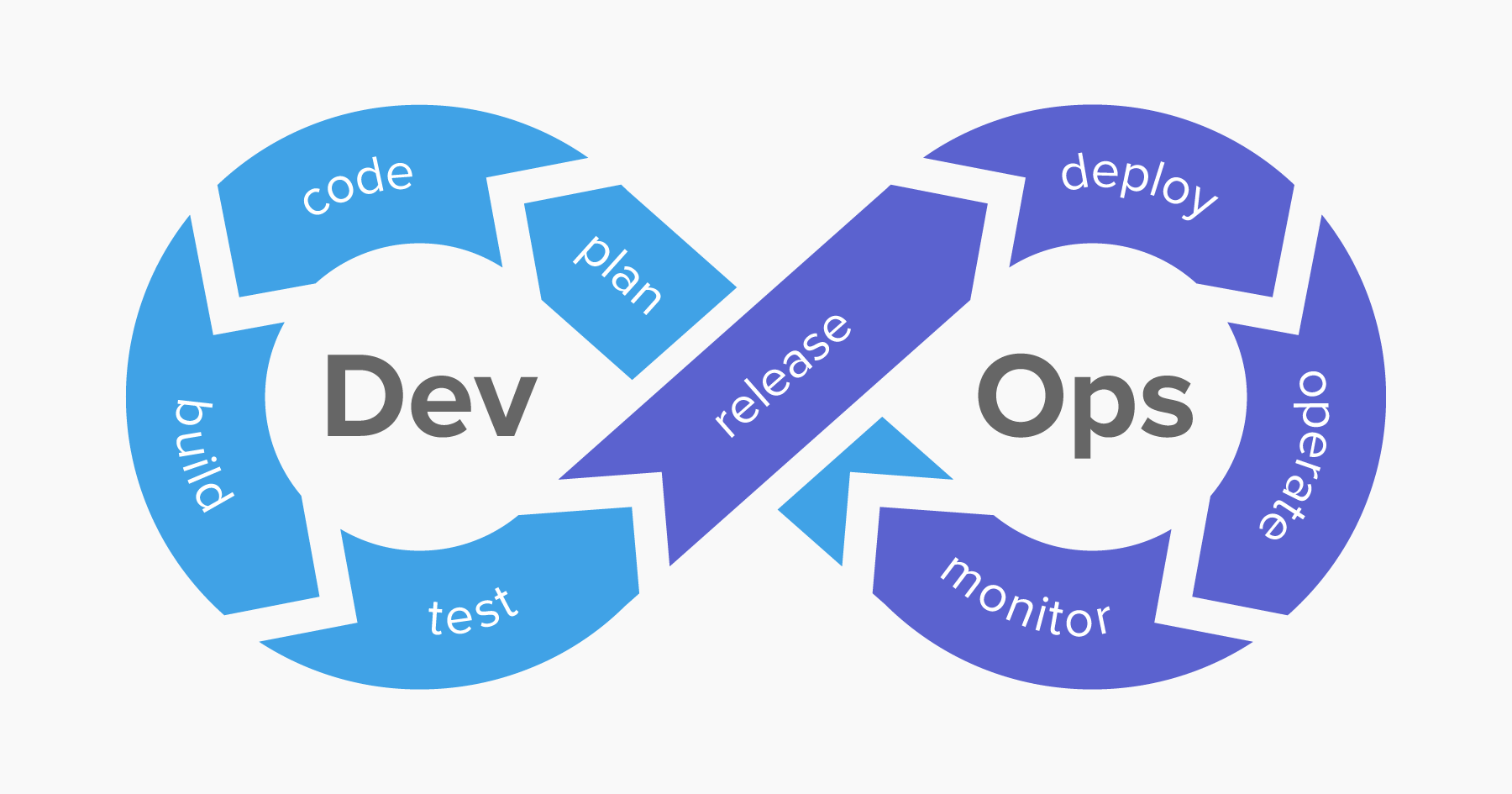 Our DevSecOps approach integrates security into development and operations throughout the product’s life cycle. We follow best practices for secure development. As part of these practices, we incorporate automated vulnerability scans into the continuous integration pipeline that provide quick feedback to developers regarding possible vulnerabilities. An automatic vulnerability scan is followed by penetration testing in the pre-production environment to identify weak spots. Throughout this process, monitoring and security reports are used to achieve continuous improvement by adopting better practices and leveraging tools for maximum security.
Our DevSecOps approach integrates security into development and operations throughout the product’s life cycle. We follow best practices for secure development. As part of these practices, we incorporate automated vulnerability scans into the continuous integration pipeline that provide quick feedback to developers regarding possible vulnerabilities. An automatic vulnerability scan is followed by penetration testing in the pre-production environment to identify weak spots. Throughout this process, monitoring and security reports are used to achieve continuous improvement by adopting better practices and leveraging tools for maximum security.

